The reason for this blog post was due to a domain migration which involved a SharePoint 2010 server. These were the symptoms, and all the steps I took to resolve them.
To start ensure you have set a new farm admin account.
E.G. stsadm -o updatefarmcredentials -userlogin domain\farmadmin -password PASSWORD This is of course under the sharepoint bin directory and wont be part of the servers default path. All Tasks moving forward will be done with this account (in my case the account has local admin rights as well as being the sharepoint farm admin permissions)
You might have come across an error such as this when working with SharePoint. Might have been from an admin removing a service account in AD, or in my case a whole domain change.
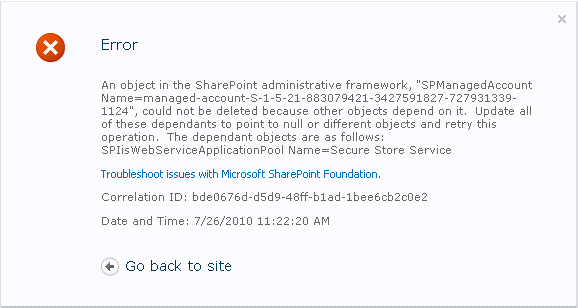
If you’re new to SharePoint you might simply panic before thinking and simply google and you might come across this.
Which sadly leads to a dead end. The reason his leads to a dead end while others have answers I’ll get to soon.
Next the simple thing you’d figure is to do as it says, reconfigure the service to run under a different account. To your dismay you discover the Central Admin page to make this change gives you this!

You might be thinking you’re in a catch 22 here. But fret not, when in doubt PowerShell. I love PowerShell and it only keeps getting better, in this case it’s our savour.
Remember when I stated that SharePoint link was a dead end. It was a dead cause there are different component types, 4 to be exact and I’m gonna tell you how to fix them all! With Sources!
First up the 4 different types!
1) Service Instance:
Cmdlet: Get-SPServiceInstance
Use the comdlet to list all SharePoint Service instances, mark the ID. Place the service instance into a variable.
E.G. $WindowsTokenService=Get-SPServiceInstance -Identity ServiceGUID
Once you have the variable, it should have a bunch of subclasses. In this case .service.ProcessIdentity. You can see it attributes by typing.
E.G. $WindowsTokenService.service.ProcessIdentity
It should display the service account used to run the service. Simply change it via
E.G $WindowsTokenService.service.ProcessIdentity.Username="Domain\NewServiceAccount"
*NOTE* This accuont needs to already be registered as a serivce account in SharePoint, either via the Central Admin page or Powershell.
Then call the object'ssubclass update and deploy methods.
E.G. $WindowsTokenService.service.ProcessIdentity.Update()
E.G. $WindowsTokenService.service.ProcessIdentity.Deploy()
That's it for basic SharePoint Service Instances.
2) Service Applications:
Cmdlet: Set-SPServiceApplicationPool
The funny part about SharePoint Service instances is theres no Set type powershell comdlete for it. Thus the cmdlet used was a Get cmdlet.
The funnt part about Service Applications is not to use the ServiceApplication cmdlet, but rather the ServiceApplicationPool cmdlets.
E.G Get-SPServiceApplicationPool -Identity SercurityTokenServiceApplicationPool | Set-ServiceApplicationPool -Account "Domain\NewServiceAccount"
Don't forget to do an IIS reset. Then running the Get-SPServiceApplicationPool cmdlet the service application should have a set PrcoessAccountName.
3) Content Applications:
Cmdlet: [Microsoft.SharePoint.Administration.SPWebService]::ContentService.ApplicationPools | ft Name
Yeah you read that right, there's no direct PowerShell cmdlet for this one. You got to go deep... real deep. Anyway run the cmdlet to list all Content Applications.
Once you have determined the one you need to change the service account for place it in a variable.
E.G. $SPAppPool=[Microsoft.SharePoint.Administration.SPWebService]::ContentService.ApplicationPools | where {$_.Name -like "My Content App Pool Name"}
Calling this variable will result in an output very similar to a Service Instance's Service.ProcessIdentity subclass. So you guessed it.
E.G. $SPAppPool.Username="Domain\NewServiceAccount"
E.G. $SPAppPool.Update()
E.G. $SPAppPool.Deploy()
4) Search Service:
Cmdlet: Get-SPEnterpriseSearchService
Yup believe it another Get cmdlet to make a change, where are these Set counterparts you may ask, well that's a good fucking question. We should ask Microsoft.
Anyway, if this hasn't annoyed you enough already chances are you haven't been a SharePoint admin for long, cause it's a rabbit hole. So to finish up here.
E.G. $SSS=(Get-SPEnterpriseSearchService).get_ProcessIdentity()
E.G. $SSS.Username="Domain\NewServiceAccount"
E.G. $SSS.Update()
E.G. $SSS.Deploy()
Sources:
General SharePoint 2010 Managed Service Accounts
Service Instances Source
Service Application Source
Content Application Source
Search Service Source
Once the Get-SPServiceAccounts shows all good on password expiry and no bad accounts exist, there should be no issues opening the Configure Managed Service Accounts section in Central Administration page of SharePoint 2010.
Happy Configuring. 🙂
To Paraphrase:
0) There is no way to paraphrase this.
1) Don’t break SharePoint.
2) Don’t break SharePoint.